A) Determine safe driver discounts
B) Predict machinery downtime
C) Reward safe driving behaviors
D) Monitor heart rate, calorie burns, sleep quality and more
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When using IoT products, companies must manage risks related to the 5Vs of big data. Choose the best definition of Veracity from the list below.
A) Inconsistencies and uncertainty in data
B) Different formats of data from various sources
C) Extract useful data
D) High speed of accumulation of data
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
"In RPA, conditional statements involve a trigger, which is a ________, and a subsequent action, or decision."
A) cause
B) scenario
C) situation
D) prompt
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Choose from the list below the best definition of cryptology.
A) Cryptology are the algorithms used to encode a message.
B) Cryptology are the algorithms used to convert an encrypted message back to its original form.
C) Cryptology are computer programs that act as intermediaries that contract, execute, and settle contracts.
D) Cryptology is the science of using a secret code for secure data communication.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
"In a ________ blockchain the intermediary comes back. A single entity governs the network."
A) private
B) public
C) consortium
D) corporate
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Reviewing the illustration below. Which word fits best for B? 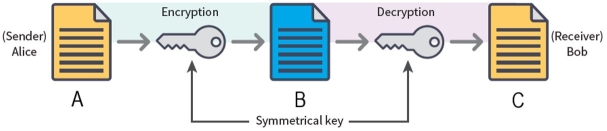
A) Plain text
B) Cipher text
C) Decrypted text
D) Simple text
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Extended reality is not a new concept. However, recently this technology has found its way into consumer's devices in an affordable and accessible manner. Choose the best definition of Mixed Reality (MR) from the list below.
A) Overlays reality with digital images
B) Hybrid combination of real and virtual objects coexisting in real time
C) Full immersion into a virtual world with virtual objects
D) Creating scenarios for employees to engage in
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When using IoT products, companies must manage risks related to the 5Vs of big data. Choose the best definition of Volume from the list below.
A) Huge amounts of data
B) Different formats of data from various sources
C) Extract useful data
D) High speed of accumulation of data
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Data retention is one of the characteristics of good data. Choose from the list below how traditional ledgers impact data retention.
A) They have the risk of subsequent manipulation.
B) Backups are far more restricted.
C) Verification of transactions may be limited to a single person.
D) A traditional ledger is not widely distributed.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Choose from the list below the best definition of Gamification.
A) Gamification is the connection of electronic devices to the internet through sensors, software, and other technologies.
B) Gamification takes three forms, which progress from completely real to completely virtual.
C) Gamification is the merger of video game principles and real-world simulations where the user can achieve badges and earn points while they learn new skills.
D) Gamification are physical devices controlled by computers using complex algorithms.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
According to the Rogers' Adoption Curve, ________% of businesses are Innovators.
A) 2.5
B) 13.5
C) 34
D) 16
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Data validity is one of the characteristics of good data. Choose from the list below how traditional ledgers impact data validity.
A) They have the risk of subsequent manipulation.
B) Backups are far more restricted.
C) Verification of transactions may be limited to a single person.
D) A traditional ledger is not widely distributed.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
According to the Rogers' Adoption Curve, ________% of businesses are Early Adopters.
A) 2.5
B) 13.5
C) 34
D) 16
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The accounting profession is evolving in response to the use of blockchain technology in business. Choose from the list below how purchasing accountants are impacted by the use of blockchain.
A) Record transactions related to buying and selling cryptocurrencies
B) Simplify and automate tax compliance and transparency
C) Secured payments are sent to suppliers as soon as materials are received.
D) Acquire sufficient evidence about the nature of blockchain transactions
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Choose from the list below the best definition of Internet of Things (IoT) .
A) Internet of Things is the collection of electronic devices to the internet through sensors, software, and other technologies.
B) Internet of Things takes three forms, which progress from completely real to completely virtual
C) Internet of Things is the merger of video game principles and real-world simulations where the user can achieve badges and earn points while they learn new skills.
D) Internet of Things are physical devices controlled by computers using complex algorithms.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
If the internal audit team is involved with a review after the new technology is adopted, we call it a
A) before-implementation review.
B) mid-implementation review.
C) pre-implementation review.
D) post-implementation review.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Choose from the list below the best definition of decryption.
A) Decryptions are the algorithms used to encode a message.
B) Decryptions are the algorithms used to convert an encrypted message back to its original form.
C) Decryptions are the computer programs that act as intermediaries that contract, execute, and settle contracts.
D) Decryption is the science of using a secret code for secure data communication.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Choose from the list below the best definition of Autonomous Things (AuT) .
A) Autonomous Things are the connection of electronic devices to the internet through sensors, software, and other technologies.
B) Autonomous Things takes three forms, which progress from completely real to completely virtual.
C) Autonomous Things are the merger of video game principles and real-world simulations where the user can achieve badges and earn points while they learn new skills.
D) Autonomous Things are physical devices controlled by computers using complex algorithms.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
"In RPA, conditional statements involve a trigger, which is a scenario, and a subsequent ________, or decision."
A) cause
B) situation
C) action
D) prompt
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
According to the Rogers' Adoption Curve, ________% of businesses are Early Majority.
A) 2.5
B) 13.5
C) 34
D) 16
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Showing 81 - 100 of 100
Related Exams